If you don’t already know, WPA-2 is not a good Wi-fi standard. Basically it can be breached through the flawed four way handshake. But now it gets even worse, and where ESET Research have published a white paper defining KrØØk (CVE-2019–15126), and which is based on the previously discovered KRACK vulnerability. Within this the researchers manage to force a device to use a “All Zeros” key, and thus decrypt all the packets sent from the device:
The research has shown that two of the most popular wifi chipset manufacters — Broadcom and Crypress — are vulnerabily to thus, which could mean that millions (or even billions) or devices are exposed to the vulnerability. These chipers are used in wifi routers and access points, and affects both home-based wifi (WPA-2 Personal) and enterprise networks (WPA-2 Enterprise).
KRACK
It’s a well-know secret, but the WPA-2 handshaking method used in your home Wi-fi system is flawed. The authentication method used is defined as WPA2-Personal, and that we need to migrate to something which is more secure. While your corporate wi-fi network (and which uses WPA3-Enterprise) is fairly bullet proof, the 4-way handshake method used on WPA2-Personal networks can be cracked with a single capture of a packet [details]:
And so, on 16 October 2017, the weakness of the four-way handshake was further highlighted with KRACK (Key Reinstallation Attacks) vulnerability [paper]:
US-CERT has become aware of several key management vulnerabilities in the 4-way handshake of the Wi-Fi Protected Access II (WPA2) security protocol. The impact of exploiting these vulnerabilities includes decryption, packet replay, TCP connection hijacking, HTTP content injection, and others. Note that as protocol-level issues, most or all correct implementations of the standard will be affected. The CERT/CC and the reporting researcher KU Leuven, will be publicly disclosing these vulnerabilities on 16 October 2017.
Within the four-way handshake, in the third step, the protocol allows for the key to be sent many times. On resending, the nonce is reused, and which compromises the handshaking, and cracks the crypto.
Meet the Simultaneous Authentication of Equals (aka Dragonfly)
And so the Simultaneous Authentication of Equals(SAE, and also typically known as Dragonfly) method has been introduced in WPA-3 Personal and which replaces with 4-way handshake with a zero-knowledge proof method (see theory later on in the article). Unfortunately the same team that defined the KRACK vulnerability has found new weaknesses in its setup [here].
Within their research, the research team found that they could recover the password used for the network, and thus steal sensitive information from the communications. These attacks were:
- Downgrade attack. This involves reducing the security level used by the protocol, and relates to the backwards comparability with WPA-2. With this we get WPA3-Transistion, and which uses the WPA-2 method to connect to the access point, and thus steal the password.
- Three side channel attacks. One of these attacks use a security group which uses a prime number of its modulo function. The attacker can then observe how long the access point takes to compute a password, and then narrow the range of possible passwords used. Another two side-channel attacks involved investigating the running memory, and where a dictionary attack could be used to analyse the patterns created. The research team estimated that they could brute-force all 8-character lowercase passwords for $125 on Amazon EC2 instances.
- Denial of service (DoS) attack. This involves side-stepping the WPA3 DoS method for detecting fake MAC addresses, and where the research team managed to bring the network down with just 16 forged connection attempts per second.
The full details of the vulnerabilities are defined here:
- CERT ID #VU871675: Downgrade attack against WPA3-Transtition mode leading to dictionary attacks.
- CERT ID #VU871675: Security group downgrade attack against WPA3’s Dragonfly handshake.
- CVE-2019–9494: Timing-based side-channel attack against WPA3’s Dragonfly handshake.
- CVE-2019–9494: Cache-based side-channel attack against WPA3’s Dragonfly handshake.
- CERT ID #VU871675: Resource consumption attack (i.e. denial of service) against WPA3’s Dragonfly handshake.
While all of these relate to WPA-3 Personal, the research team also found a bug in the EAP-PWD protocol, and where an intruder could impersonate a user on a network, without knowing their password. This bug affects WPA-3 Enterprise, as it focuses on RADIUS integration. Details have not been released at the current time on this.
Dragonfly
It has been known for a while that the core of Wi-fi — WPA-2 (IEEE 802.11i) — is weak in its implementation of security. While its cryptography is sound — using AES encryption — its main weakness focuses on the flawed 4-way handshake.
Within this, the client and access point pass a hashed value of the SSID and the password, and this can be seen by an intruder. Its saving grace is that the hashing method used — PBKDF2 — is a relatively slow method, and when it was initially rolled-out it would have been relatively expensive to crack it. Unfortunately, these days, cloud crackers can now run at high speeds, and even PBKDF2 can be cracked within reasonable time limits and for a minimal cost.
The great worry, though, is that once it is cracked, it is cracked for the whole network. With 16-GPU clusters available to rent within AWS for less than $10 per hour, the opportunity exists for the core of wi-fi to fundamentally fail within the next few years.
And so, the Wi-Fi Alliance has addressed this fundamental problem with the release of WPA-3, and where the 4-way handshake is replaced by a zero-knowledge proof method named Simultaneous Authentication of Equals (SAE). Its roots derive from mesh networks and of the Dragonfly protocol, and have since been defined in IEEE 802.11s.
SAE
The focus for SAE is to properly authenticate a device onto a network and using a password and MAC addresses to authenticate. An intruder should not be able to connect to a network unless they known password that the access point uses. Also, an intruder should not be able to guess either the password or the long-term authentication element of the password. In WPA-2 an intruder can listen to the 4-way handshake and can then brute force the password from hashed value created (see the section below for details).
With SAE — and which is based on a zero-knowledge proof known as dragonfly — we use the Diffie-Hellman key exchange method but adds an authentication element. With this we create a shared key with elliptic curve methods (NIST curves), and then use a pre-shared key and MAC addresses. When the client connects to the access point, they perform an SAE exchange. If successful, they will each create a cryptographically strong key, of which the session key will be derived from. If one session key is cracked it will only affect one key, and not all of the key used, as with WPA-2.
The basic method
Basically a client and access point goes into phases of commit and then confirm. Once we have a commitment, the client and access point can then go into the confirm states each time there is a session key to be generated. The method uses forward secrecy, where an intruder could crack a single key, but not all of the other keys.
The core security comes from the power of discrete logarithms and where it is difficult to find the value of x, even though we have Y, G and p:
Y = Gˣ mod q
and where q is a prime number. We make q a prime number as it allows us to perform maths functions, while constraining the value between 0 and q-1 [finite fields].
In the commit phase, Alice (the client) generates two random values (a,A), and then computes a scalar value (a+A). The value that Alice will pass is the PE (Password Equivalent — such as hashed value of the password that Bob and Alice know) raised to the power of -A. As the values will get large, the operations are done with (mod q) and where q is a large prime number.
Bob does the same, and then they exchange values. In the end they will have the same shared commit key (PEªᵇ). They will only have the same shared value, if they have both used the same password. This password is thus used to validate Bob and Alice, and they will only have the shared shared commit value if they both have the same password. The intruder cannot determine either the original password or the final shared value.
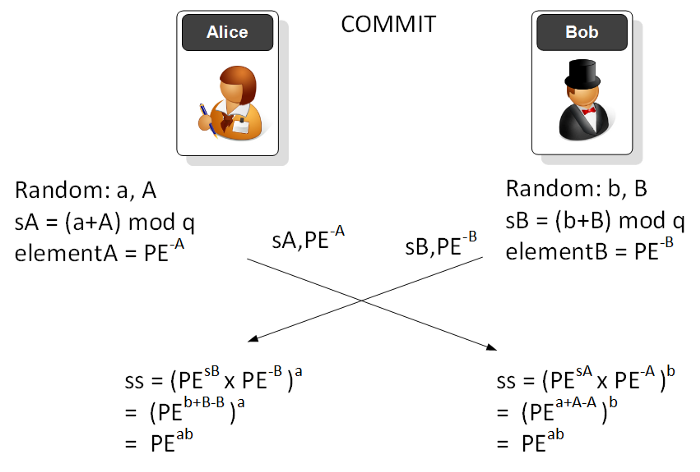
To perform the -A power, we perform an inverse mod q function (and which uses the extended euclidean algorithm) [inverse mod function]:
elementA = inverse_of(pow(PE,A),q)
elementB = inverse_of(pow(PE,B),q)
In the confirm phase we then use the long-term key to generate a unique session key. An attacker cannot determine the password used or the long-term master key (PMK). The cracking of one session key will also not reveal the rest of the keys which have been used (forward security). This is not the case for WPA-2.
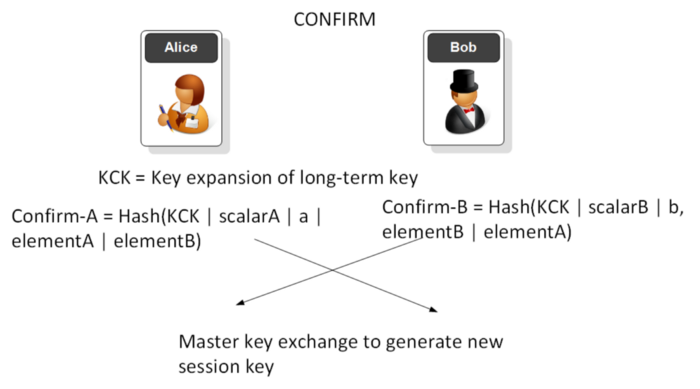
Confirmation phase
Here is a simple implementation of the Dragonfly method [here]:
import hashlib
import randomdef extended_euclidean_algorithm(a, b):
"""
Returns a three-tuple (gcd, x, y) such that
a * x + b * y == gcd, where gcd is the greatest
common divisor of a and b.This function implements the extended Euclidean
algorithm and runs in O(log b) in the worst case.
"""
s, old_s = 0, 1
t, old_t = 1, 0
r, old_r = b, awhile r != 0:
quotient = old_r // r
old_r, r = r, old_r - quotient * r
old_s, s = s, old_s - quotient * s
old_t, t = t, old_t - quotient * treturn old_r, old_s, old_tdef inverse_of(n, p):
"""
Returns the multiplicative inverse of
n modulo p.This function returns an integer m such that
(n * m) % p == 1.
"""
gcd, x, y = extended_euclidean_algorithm(n, p)
assert (n * x + p * y) % p == gcdif gcd != 1:
# Either n is 0, or p is not a prime number.
raise ValueError(
'{} has no multiplicative inverse '
'modulo {}'.format(n, p))
else:
return x % pq=131
a=random.randint(1,1000)
b=random.randint(1,1000)
A=random.randint(1,1000)
B=random.randint(1,1000)sA= a + A
sB = b + Btext="hello"
PE = int(hashlib.md5(text).hexdigest()[:8], 16)elementA = inverse_of(pow(PE,A),q)
elementB = inverse_of(pow(PE,B),q)PEsA = pow(PE,sA,q)
PEsB = pow(PE,sB,q)print "Element A:",elementA
print "Element B:",print elementBss1 = pow(PEsA * elementA,b,q)
ss2 = pow(PEsB * elementB,a,q)print "Alice share:",ss1
print "Bob share:",ss2
A sample run is [here]:
Password: hello
Alice generates two random values
a: 419
A: 467Bob generates two random values
b: 858
B: 608Alice calculates elementA
Element A: 347Bob calculates elementA
Element B: 227They exchange values and calculate a secret shareAlice share: 151
Bob share: 151
You can see I have taken a hash of the password, and then converted it into an integer, so that I can use operate on it with logs:
text="hello"
PE = int(hashlib.md5(text).hexdigest()[:8], 16)
The operation of performing a power (PEˣ and mod q) is achieved with a single (and fast) operation with Python:
PEsB = pow(PE,x,q)
Conclusions
The WPA2-Personal protocol has a fundamental weakness, and it looks like there could be problems with WPA3-Personal. Hopefully these will get fixed, but WPA2-Personal will be retired forever. For some reason, when systems are created, the requirement to get things to the market often trumps the requirement for security testing.
